Reasonable disclosure grace periods for security vulnerabilities in vehicle software
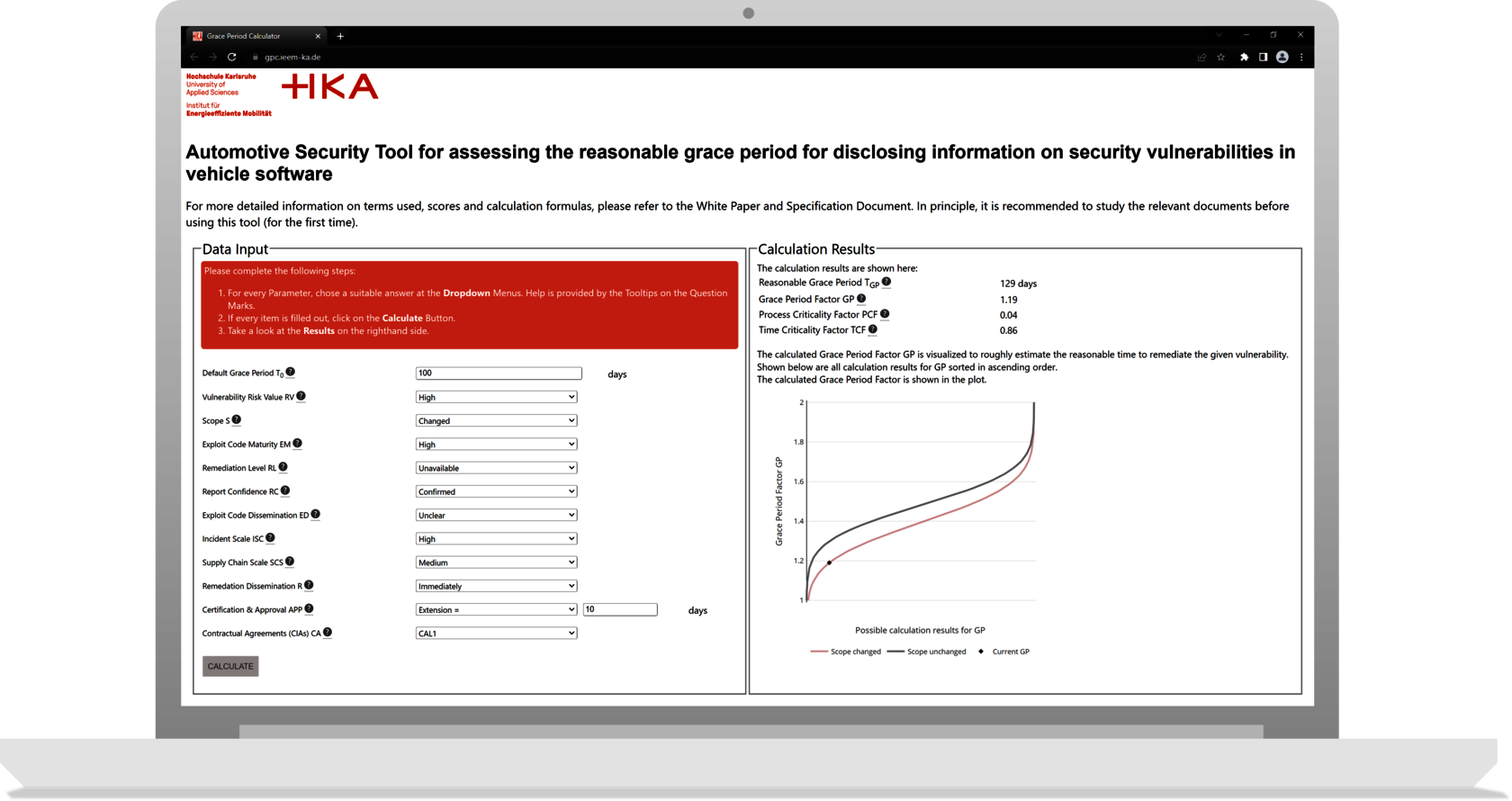
For many years, the number of detected cyber-attacks assigned to the automotive sector has been growing steadily. With the integration of intrusion detection and prevention systems (IDPS), the amount of information processed about cyber incidents is expected to increase significantly, making efficient incident response management (IRM) necessary. In addition to the categorization of security events, the rapid prioritization and remediation of detected vulnerabilities will also gain in importance. Time is of the essence when reacting to vulnerabilities. With UN regulation R155 coming into force in 2021, the implementation of processes for IRM has become relevant for type approval for all OEMs in many parts of the world. Accordingly, the implementation of processes capable of detecting cyber incidents and responding to vulnerabilities must be demonstrated. The regulation demands response within a ’reasonable time frame’. We provide a tool to make assessment of the reasonable remediation time for automotive software vulnerabilities quantifiable. Thus, we introduce an objectifiable metric that can harmonize vulnerability management and disclosure more efficient. Potential use cases for our tool are prioritization of vulnerability remediation actions, as well as assessment of appropriate grace periods in the context of Coordinated Vulnerability Disclosure (CVD) processes. learn more
You are a CVD process coordinator or car manufacturer.
Use our tool to assess time- & process criticality of the disclosure process
and make timelining transparent,
reasonable and fair for all stakeholders.
Avoiding 0-day disclosure
Harmonization and escalation prevention through transparent evaluation criteria.
Resource efficient
More efficient vulnerability prioritization by including process criticality.
SecForCARs compliant
Driving mitigation of vulnerabilities in reasonable timeframes.
Use the WebTool now
Unlicensed and free to use
Our tool and the underlying metric are unlicensed and free to use and modify. A continuous improvement and further development process by the community is explicitly desired. We ask everyone interested to communicate changes and improvements to the calculation tool or the underlying metric with us.
Background and overall context
The UN regulation R155 demands response to vulnerabilities in vehicle software within a 'reasonable time frame'. However, precise specifications as well as an evaluation basis for adequacy is not given. Efficient Incident Response Management (IRM) may require cooperation along the supply chain with as little friction as possible. An industry-wide common understanding of the term 'reasonableness' is necessary to implement a corresponding internal resource allocation. From our point of view, there is a lack of sufficient experience and data in the automotive sector to evaluate 'reasonableness'.
Use our tool to make assessment of the reasonable remediation time for automotive software vulnerabilities quantifiable.
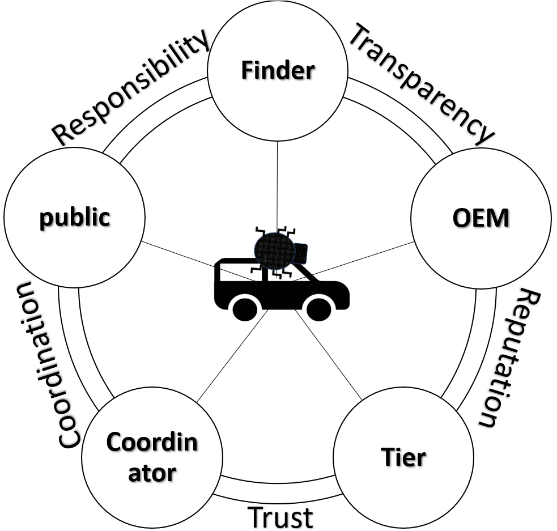
Use Case CVD
A CVD program can help to continuously maintain or enhance the cybersecurity of a product during its lifetime. Various strategies have been established in practice for the disclosure of vulnerabilities. ISO/IEC 29147 standardizes these processes with the goal of minimizing 0-day disclosures and thus potential threats from exploits.
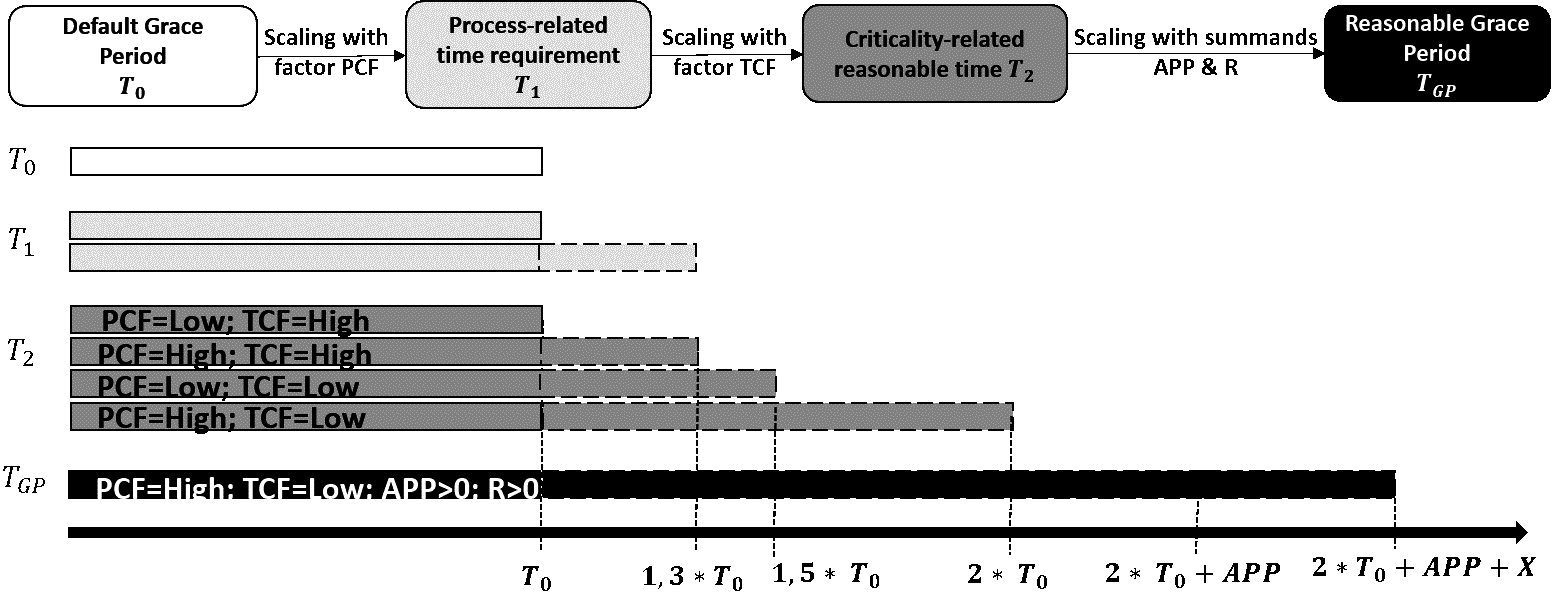
Stakeholders (see Figure beside) perspectives and expectations on a Coordinated Vulnerability Disclosure (CVD) process may differ. A key goal is to prevent escalations such as 0-day disclosure or even exploits. Harmonizing the understanding of the appropriate remediation time or the associated disclosure period (grace period) can help prevent escalation. For this to happen, there needs to be a common understanding of which assessment criteria are valid. Our cross-industry research has shown that blanket, strict grace periods for disclosing information on -at worst- unaddressed vulnerabilities are often specified1. This procedure could lack a consideration of the appropriateness for a given individual vulnerability (escalation management). Especially for enormously safety relevant and complex systems-of-systems such as vehicles, the blanket definition of strict deadlines does not seem to be appropriate and even negligent. We welcome the handling of the Automotive Security Research Group (ASRG)2, which specifies a fixed grace period of 90 days, but explicitly allows leeway when it makes sense. Our tool builds on this by defining valid criteria to reasonably measure this leeway.
Our tool enables the determination of individual grace periods that address the time and process criticality of an individual CVD process, rather than setting blanket strict and unreasonable deadlines.
| 1 | Rapid7 Disclosure Policy. www.rapid7.com/security/disclosure/ Project Zero Disclosure Policy. googleprojectzero.blogspot.com/2020/01/policy-and-disclosure-2020-edition.html CERT/CC Disclosure Policy. vuls.cert.org/confluence/display/Wiki/Vulnerability+Disclosure+Policy. Zero day Initiative Disclosure Policy. www.zerodayinitiative.com/advisories/disclosure_policy/ |
| 2 | ASRG Disclosure Policy. asrg.io/disclosure/ |
Further documents & links
Our Security-Projects
Some publications
- Bolz R: Evaluating reasonable patching times for security product vulnerabilities in the automotive field. In: Feßler D, Kettner M, Kriesten R, Nenninger P, Offermann P (Hrsg.): Reports on Energy Efficient Mobility. 3 Aufl., 2023, S. 140-156 (Elektronische Veröffentlichung: dx.doi.org/10.5281/zenodo.7573669)
- Can Kaya U, Bolz R: Survey on Vulnerability Report Handling in the Automotive Environment. In: Feßler D, Kettner M, Kriesten R, Nenninger P, Offermann P (Hrsg.): Reports on Energy Efficient Mobility : Volume 2. 2022 (Reports on Energy Efficient Mobility 2), S. 17-31 (Elektronische Veröffentlichung: doi.org/10.5281/zenodo.6373380)
- Bolz, R., Kriesten, R.: Automotive Vulnerability Disclosure: Stakeholders, Opportunities, Challenges. In: Journal of Cybersecurity and Privacy, ISSN 2624-800X, Vol. 1 (2021), Nr. Issue 2, 14 S. (Elektronische Veröffentlichung: doi.org/10.3390/jcp1020015)
- Bolz, R., Ahmed, R.,: Continuous Maintenance of Automotive Security in the Post-Production Phase through Coordinated Vulnerability Disclosure. Vol. 1 Aufl., Zenodo 2021, 55 S. (Elektronische Veröffentlichung: doi.org/10.5281/zenodo.4569338)
- Sommer F, Rumez M, Dürrwang J, Bolz R, Kriesten R: Enhancement of Cyber Security for Cyber Physical Systems in the Automotive Field Through Attack Analysis. In: Embedded World Exhibition & Conference ... it's a smarter world. Embedded World Exhibition & Conference (Nuremberg, 25.-27.02.2020), Haar: Weka Fachmedien 2020, 7 S.- ISBN 978-3-645-50186-6
- Bolz R, Dürrwang J, Rumez M, Sommer F, Kriesten R: Unterstützung der Security-Entwicklung von Fahrzeugen durch Angriffsanalysen. In: Forschung aktuell, ISSN 1613-4958 (2020), S. 28-33 (Elektronische Veröffentlichung: Forschung aktuell 2020)
Interested in a Research Cooperation?
Feel free to contact us!
Karlsruhe
Institut für Energieeffiziente Mobilität (IEEM)
Moltkestr. 30
76133 Karlsruhe
Post >
Institut für Energieeffiziente Mobilität (IEEM)
Postfach 2440
76012 Karlsruhe