SecForCARs – Security For Connected, Autonomous CARs
Security against cyber attacks is one of the greatest challenges in the development of modern vehicles. In the case of highly complex, autonomous vehicles, protection against such attacks is particularly relevant, as in the worst case scenario the health of the vehicle occupants and other road users can be endangered. Here, it must be ensured above all that integrated security measures function reliably and that no critical security gaps have been overlooked. How such security tests can be carried out early in development and how to deal with any security gaps found is being investigated by Karlsruhe University of Applied Sciences as part of the SecForCARs project.
Karlsruhe University of Applied Sciences tests the IT security of networked, autonomous vehicles for the overall SecForCARs project and manages any security vulnerabilities found.
The joint project SecForCARs (Security For Connected Autonomous caRs) consists of a consortium of research institutions and industry partners and deals with IT security of connected autonomous vehicles. The Karlsruhe University of Applied Sciences focuses on increasing the reliability of such vehicles. One area concerns the verification and validation of vehicle security and deals with testing the security of autonomous vehicles, taking into account existing security attacks and threat and risk analyses that have already been carried out.
Security-Testing
A security test can be considered as an attack on the vehicle, as both processes have the goal of violating security features. The security tester achieves the detection of vulnerabilities, which can then be eliminated by the vehicle manufacturer. The attacker, on the other hand, wants to take advantage of the attack. In the worst case, this can endanger the occupants or the surrounding traffic. Security testing thus plays a major role in securing vehicles.
Currently, however, tests only take place at the end of the product development process, when a vehicle is about to be delivered to the customer or is already in operation. This poses the risk that any vulnerabilities found can only be eliminated at great expense, which would lead to increased development costs.
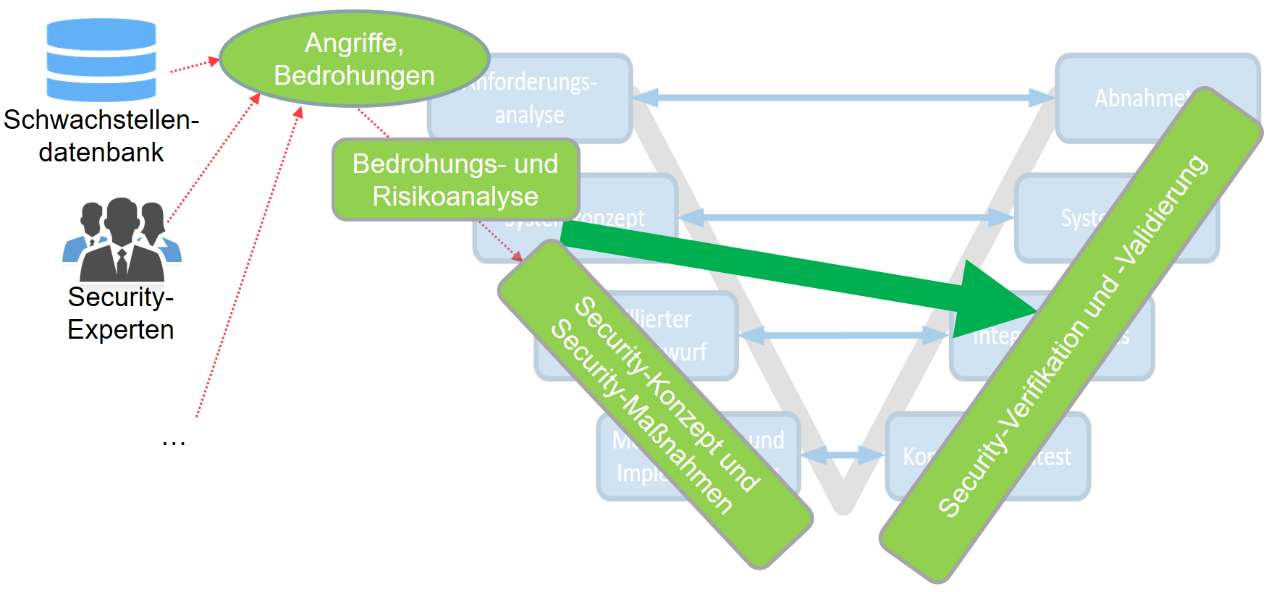
For this reason, security tests should take place in early phases of the development process in order to be able to eliminate potential vulnerabilities as early as possible. The development of a test methodology that does this is being developed in the SecForCARs project by Karlsruhe University of Applied Sciences. The basic concept of this method is shown in Figure 1.
First, already published security vulnerabilities and attacks are collected and analysed. Based on these attacks, a threat and risk analysis is then carried out. This serves to examine the feasibility of the attacks and to determine their probability of occurrence. Subsequently, it will be examined how such an analysis methodology can be extended to specify test cases and derive them in the further course. The basis for this is an examination of various test tools and their classification in the different test levels.
Research at IEEM
In addition to security testing, the work at IEEM also focuses on improving cyber security during operation in the field. An exemplary concept for dealing with security vulnerabilities is being developed, which ranges from the reporting of a discovered vulnerability to its communication and remediation with other potentially affected manufacturers. Following this process, relevant information on the fixed vulnerabilities will be stored in an automotive vulnerability database. This should not only promote fair cooperation between white-hat hackers and security research with industry, but also build up a sound database of vulnerability information in the long term, which can be used for threat analysis and security testing (industry, research), for example, but also for compiling statistics and analyses on the development of the automotive security environment (authorities, legislation).
A look at IT security shows how this can be achieved.
In the field of information technology, questions about how to deal with security vulnerabilities have been discussed for decades. Corresponding standards such as ISO/IEC 29147 and ISO/IEC 30111 are now widely accepted and applied. Research into various concepts that have emerged over the years in the IT domain and the examination of possibilities to adapt these to the automotive domain are an essential part of the research work at IEEM. The aim is to work out the differences in the given requirements between the IT and automotive domains and to adapt solutions accordingly. For example, the greatest challenges for the vehicle domain are the enormous safety relevance, the complex vertical and horizontal supplier structures, the pronounced non-locality of the target system vehicle (updating), the long product life cycles, and the relatively low computing power of vehicle control units (cryptography). These requirements, in turn, coincide with those of the aviation domain.
Goals
- The result of this project is an integrated test process that makes it possible to derive test cases on the basis of published attacks and the implementation of a threat and risk analysis. These are used to test vehicles at all test levels using various test tools. Finally, the methodology will be evaluated using a demonstrator (Device Under Test).
- Another goal is to implement the concepts found for automotive vulnerability disclosure and database in the form of two demonstrators. Firstly, an intuitive, user-friendly reporting platform in the form of a web application is to be created, which will enable finders of vulnerabilities to contact the affected manufacturer or a third independent entity on an equal footing through secure communication (PGP, S/MIME) and initiate a process for remediation and coordinated publication of the reported vulnerability. In a second demonstrator, a system of databases is to be implemented that contains vulnerability information from the notification to the (partially) publicly accessible information on fixed vulnerabilities.
Key data
Karlsruhe
Institute of Energy Efficient Mobility (IEEM)
Moltkestr. 30
76133 Karlsruhe
Post >
Institute of Energy Efficient Mobility (IEEM)
Postfach 2440
76012 Karlsruhe